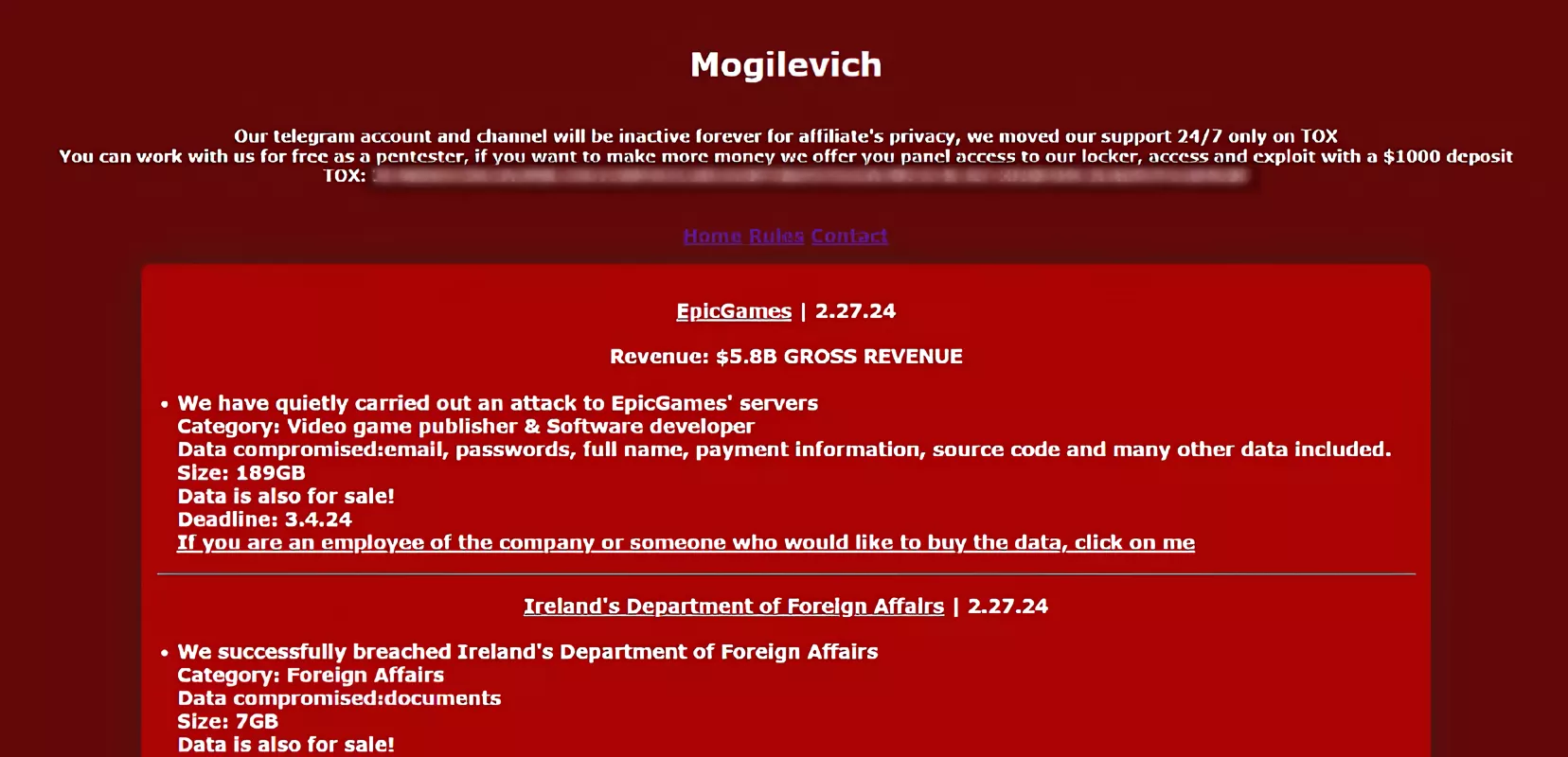
What just happened? A ransomware group is claiming to have successfully targeted Epic Games, stealing almost 200GB of data from the Fortnite maker. The stolen information is said to include emails, passwords, full names, payment information, source code, and more. The data is currently available to buy, but only until March 4.
Update: Epic Games has given the following statement regarding the alleged attack.
We are investigating but there is currently zero evidence that these claims are legitimate. Mogilievich has not contacted Epic or provided any proof of the veracity of these allegations. When we saw these allegations, which were a screenshot of a darkweb webpage in a Tweet from a third party, we began investigating within minutes and reached out to Mogilevich for proof. Mogilevich has not responded. The closest thing we have seen to a response is this Tweet, where they allegedly ask for $15k and “proof of funds” to hand over the purported data.
The gang, which goes by the name Mogilevich, posted news of the claimed hack on its darknet leak site, writes Cyber Daily. “We have quietly carried out an attack to [sic] Epic Games’ servers,” the message reads.
It’s unclear if the 189GB of stolen data comes from Epic Games customers, employees, or a mix of both. Mogilevich is offering the data for sale to Epic employees or anyone else who would like to buy it. The group never specified how much it wants, but it did say that the deadline for purchase is March 4, after which time it will likely be made publicly available.
It’s important to note that Mogilevich has not posted any evidence supporting its claim of a successful attack. On December 12, a ransomware gang called Rhysida posted what appeared to be limited evidence supporting its allegation that it had hacked Insomniac Games, maker of the Ratchet & Clank and Marvel’s Spider-Man series. With the company refusing to pay the ransom, which started at 50 Bitcoins (approximately $2 million), and the deadline having passed, Rhysida uploaded 1.67 terabytes of data containing more than 1.3 million files. Much of the leak related to the upcoming Wolverine game.
Mogilevich is a relatively new player on the ransomware scene. If the Epic hack proves true, it would only be the group’s fourth victim, the first being Nissan subsidiary Infiniti USA on February 20, 2024. It appears to be Russian-speaking and, like LockBit, advertises itself as a ransomware-for-hire operation.
In other LockBit news, last week saw the world’s most prolific gang hit by an international law enforcement operation. The group’s website was taken over and its operations were disrupted. Less than a week later, however, LockBit said it had restored its servers and was back in the cybercrime business, adding that it would target more governmental organizations going forward to test the authorities’ capabilities.