
Windows 11 will let admins mandate SMB client encryption for all outbound connections, starting with today’s Windows 11 Insider Preview Build 25982 rolling out to Insiders in the Canary Channel.
SMB encryption provides data end-to-end encryption and can be enabled on a per-share basis for the entire file server or when mapping drives using Windows Admin Center, Windows PowerShell, or UNC Hardening.
This capability was first included with SMB 3.0 on Windows 8 and Windows Server 2012, and it introduced support for AES-256-GCM cryptographic suites with Windows 11 and Windows Server 2022.
By requiring that all destination servers support SMB 3.x and encryption, Windows admins can ensure that the clients can only establish a connection if these conditions are met to defend against eavesdropping and interception attacks.
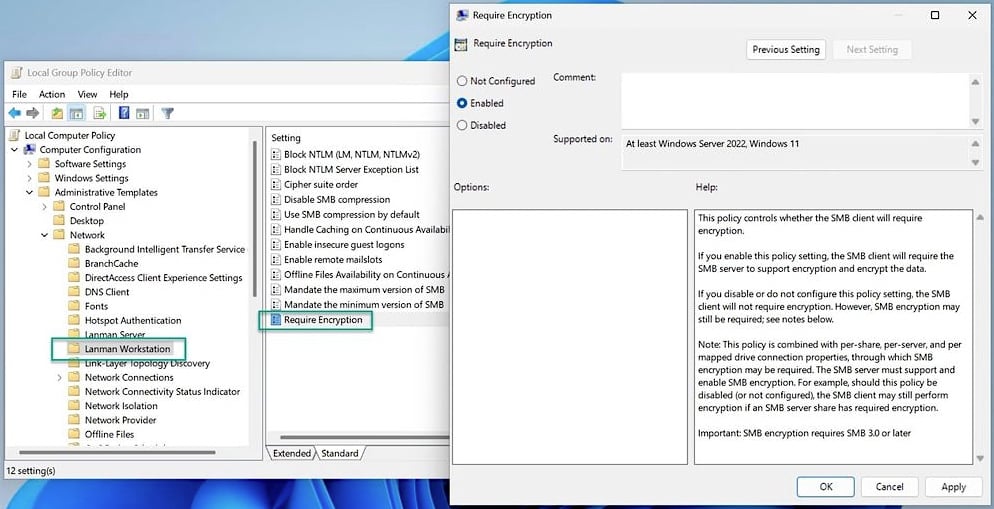
“You can now also configure the SMB client to always require encryption, no matter what the server, share, UNC hardening, or a mapped drive requires,” said Microsoft Principal Program Manager Ned Pyle.
“This means an administrator can globally force a Windows machine to use SMB encryption – and therefore SMB 3.x – on all connections and refuse to connect if the SMB server does not support either.”
The new option can be configured using PowerShell or the ‘Require encryption’ group policy under Computer Configuration \ Administrative Templates \ Network \ Lanman Workstation.
Starting with Windows 11 Insider Preview Build 25951, admins can configure Windows systems to automatically block sending NTLM data over SMB on remote outbound connections to fend off pass-the-hash, NTLM relay, or password-cracking attacks.
When toggled on, it prevents the user’s hashed password from being sent to remote servers, effectively thwarting these attacks.
With the release of Windows 11 Insider Preview Build 25381 to the Canary Channel, Microsoft also began requiring SMB signing (aka security signatures) by default for all connections to defend against NTLM relay attacks.
SMB signing, introduced in Windows 98 and 2000, has been updated in Windows 11 and Windows Server 2022 to enhance protection and performance by significantly increasing data encryption speeds.
“SMB encryption has performance overhead and compatibility overhead, and you should balance that against SMB signing – which has better performance and tamper protection but no snooping protection – or against no use of encryption or signing at all, which has best performance but no security,” Pyle said.
“SMB encryption supersedes SMB signing and supplies the same level of tamper protection, meaning that if your SMC client requires signing, SMB encryption turns it off; there is no point requiring both because encryption wins.”
These improvements are part of a broader effort to bolster the security of Windows and Windows Server, as underscored by earlier announcements from last year.
In April 2022, Microsoft marked a milestone by revealing the final phase of disabling the decades-old SMB1 file-sharing protocol for Windows 11 Home Insiders.
Building on this progress, the company also strengthened defenses against brute-force attacks by introducing an SMB authentication rate limiter, which mitigates the impact of unsuccessful inbound NTLM authentication attempts.

