
CISA and partner cybersecurity agencies and intelligence services warned that the APT29 hacking group linked to Russia’s Foreign Intelligence Service (SVR) has been targeting unpatched TeamCity servers in widespread attacks since September 2023.
APT29 is known for breaching several U.S. federal agencies following the SolarWinds supply-chain attack they orchestrated three years ago.
They also targeted the Microsoft 365 accounts of multiple entities within NATO countries as part of their efforts to access foreign policy-related information and were linked to a series of phishing campaigns aimed at governments, embassies, and high-ranking officials across Europe.
The TeamCity security flaw they’re exploiting in these attacks is identified as CVE-2023-42793 and rated with a critical severity score of 9.8/10, which unauthenticated threat actors can exploit in low-complexity remote code execution (RCE) attacks that don’t demand user interaction.
“By choosing to exploit CVE-2023-42793, a software development program, the authoring agencies evaluate the SVR could benefit from access to victims, particularly by allowing the threat actors to compromise the networks of dozens of software developers,” CISA warned today.
“The SVR has, however, been observed using the initial access gleaned by exploiting the TeamCity CVE to escalate its privileges, proceed laterally, deploy additional backdoors, and take other steps to ensure persistent and long-term access to the compromised network environments.
“While the authoring agencies evaluate the SVR has not yet used its accesses to software developers to access customer networks and is likely still in the preparatory phase of its operation, having access to these companies’ networks presents the SVR with opportunities to enable hard-to-detect command and control (C2) infrastructure.”
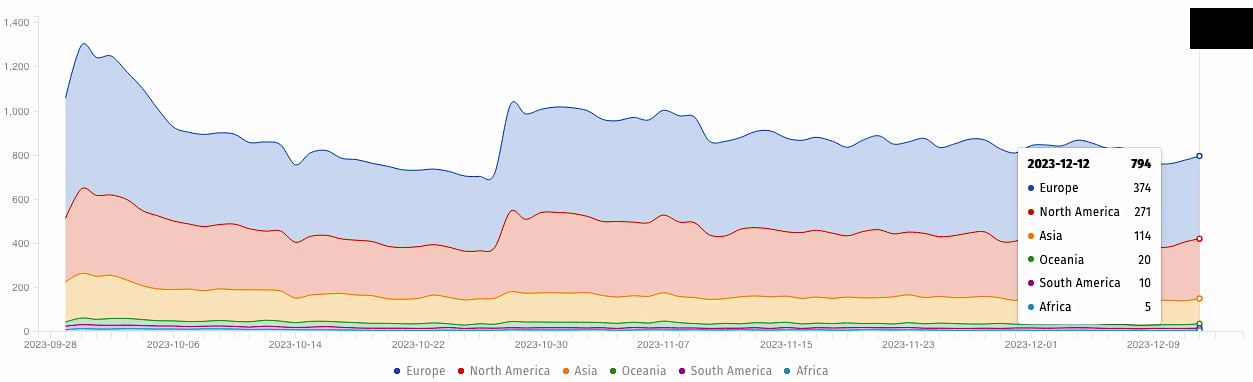
Almost 800 servers still vulnerable to attacks
Researchers from the Swiss security firm Sonar, who discovered and reported the flaw, also published technical details a week after JetBrains released TeamCity 2023.05.4 on September 21st to address the critical issue.
“This enables attackers not only to steal source code but also stored service secrets and private keys,” Sonar explained.
“And it’s even worse: With access to the build process, attackers can inject malicious code, compromising the integrity of software releases and impacting all downstream users.”
Security researchers at nonprofit internet security outfit Shadowserver Foundation are tracking almost 800 unpatched TeamCity servers that are vulnerable to attacks.
Also exploited by ransomware gangs and North Korean hackers
In early October, several ransomware gangs were already exploiting the vulnerability to breach corporate networks, according to threat intelligence companies GreyNoise and PRODAFT.
GreyNoise detected attacks from 56 different IP addresses as part of coordinated efforts aimed at breaching TeamCity servers left unpatched.
Two days earlier, the company also cautioned there’s a high likelihood that organizations that neglected to ensure their servers before September 29th have already been breached.
Microsoft later said that the Lazarus and Andariel North Korean state-backed hacking groups were backdooring victims’ networks using CVE-2023-42793 exploits, likely in preparation for software supply chain attacks.
JetBrains says developers use its TeamCity software building and testing platform at over 30,000 organizations worldwide, including high-profile ones admire Citibank, Ubisoft, HP, Nike, and Ferrari.

