Thousands of Ivanti Connect Secure and Policy Secure endpoints remain vulnerable to multiple security issues first disclosed more than a month ago and which the vendor gradually patched.
The flaws are CVE-2024-22024, CVE-2023-46805, CVE-2024-21887, CVE-2024-21893, and CVE-2024-21888. Their severity ranges from high to critical and they concern authentication bypass, server-side-request forgery, arbitrary command execution, and command injection problems.
Some of these vulnerabilities have been reported as exploited by nation-state actors before they were being leveraged at a larger scale by a broad range of threat actors.
Starting with CVE-2024-22024, the issue is an XXE vulnerability in the SAML component of Ivanti Connect Secure, Policy Secure, and ZTA gateways that allowsunauthorized access to restricted resources.
First disclosed last week and with no active exploitation confirmed yet, the vendor advised that it’s critical to immediately apply available security updates or mitigations, if there is no patch available.
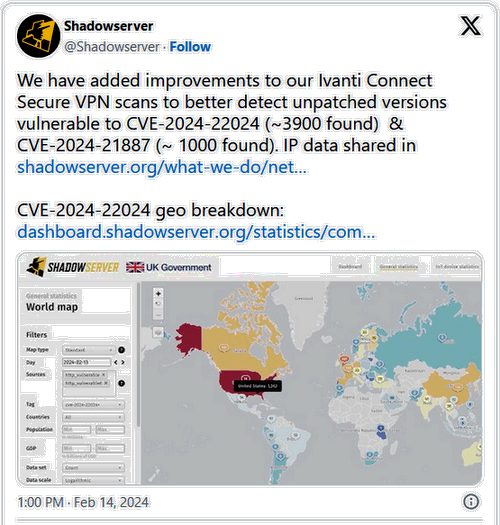
Threat monitoring service Shadowserver reports that its internet scans show more than 3,900 Ivanti endpoints vulnerable to CVE-2024-22024. Most of them are in the United States (1,262).
The organization saw roughly 1,000 Ivanti endpoints that are still vulnerable to CVE-2024-21887, a flaw that lets authenticated admins execute arbitrary commands on vulnerable appliances by sending specially crafted requests.
The vulnerability was first disclosed as a zero-day on January 10, 2024, and was reportedly exploited by Chinese hackers, along with CVE-2023-46805, an authentication bypass issue.
Yutaka Sejiyama, a security researcher at Macnica, shared his Shodan scan results with BleepingComputer earlier today, reporting that as of February 15, 2024, 00:15 UTC, there were 13,636 Ivanti servers that had yet to apply patches for CVE-2024-21893, CVE-2024-21888, CVE-2023-46805, and CVE-2024-21887.
Security updates for these four vulnerabilities were made available by Ivanti well over a month ago on January 31, 2024.
According to the researcher, the total number of internet-exposed Ivanti servers is 24,239, meaning that more than half of them remain unpatched.
Regarding CVE-2024-22024, which was disclosed and fixed on February 8, 2024, Sejiyama’s research shows a global patching percentage of only 21.1% as of today, leaving 19,132 servers exposed to the dangerous unauthorized access flaw.
Unfortunately, the flaws affecting Ivanti products were disclosed over a short period, giving administrator little time to prepare for applying the patches.
This complicates remediation efforts and heightens the risk of Ivanti systems being left vulnerable for prolonged periods, providing threat actors with a large list of potential victims.