
The official Netgear and Hyundai MEA Twitter/X accounts (together with over 160,000 followers) are the latest hijacked to push scams designed to infect potential victims with cryptocurrency wallet drainer malware.
While Hyundai has already regained access to their account and has cleaned up the timeline of all links pointing X users to malicious websites, Netgear has yet to take control of theirs, with some of the attacker’s tweet replies still available.
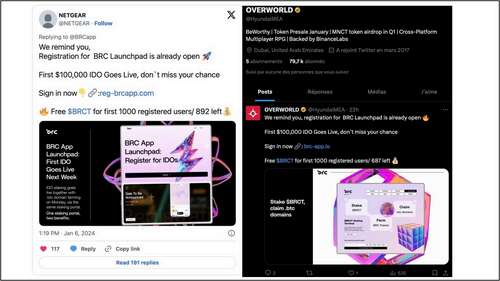
The attackers renamed the account of Hyundai MEA (Middle East & Africa) to impersonate Overworld, which describes itself as a “cross-platform multiplayer RPG, backed by Binance Labs, the venture capital and incubator arm of the Binance cryptocurrency exchange.
Likely because it’s frequently impersonated in similar scams, Overworld often warns its Twitter followers, saying, “Please exercise caution and stay clear of those impersonating our account. Only click links from the official @OverworldPlay twitter account.”
Netgear’s account has been hijacked since at least January 6th and was only used to reply to BRCapp tweets, luring followers to a malicious website promising to give the first 1,000 newly registered users $100,000.
However, anyone who connected their wallets to the site would have had their assets and NFTs stolen by the threat actors.
Netgear and Hyundai spokespersons were not immediately available for comment when contacted by BleepingComputer earlier today.
Twitter users under siege
Hackers are increasingly targeting and compromising verified government and business X accounts with ‘gold’ and ‘grey’ checkmarks to add legitimacy to their malicious tweets pushing cryptocurrency scams, phishing sites, and sites dropping crypto drainers.
For instance, the X account of web3 security firm CertiK was hacked to push a crypto drainer on Friday, while the account of Google subsidiary and cybersecurity firm Mandiant was hijacked on Wednesday, although it had two-factor authentication (2FA) toggled on.
Previously, scammers used the official Twitter account for Bloomberg Crypto to lure almost its 1 million followers to a malicious website designed to steal their Discord credentials.
As blockchain threat analysts at ScamSniffer revealed in December, a single waller drainer known as ‘MS Drainer’ stole roughly $59 million worth of cryptocurrency from 63k people in a Twitter ad push between March and November.
X users are also under a constant barrage of malicious cryptocurrency ads redirecting to fake airdrops, various scams, and, of course, crypto drainers.
Since X says it shows ads based on each user’s interests, those not linked to other cryptocurrency accounts may not see these malicious ads.
However, those in the crypto space are now besieged by what looks like a neverending torrent of such malicious ads, as BleepingComputer reported over the weekend.

