In brief: Were you recently informed that someone has tried to use your login credentials to access a site? If so, it could be related to a massive database of 71 million unique credentials that have been circulating online for a few months now, a huge chunk of which was pilfered using stealer malware.
News of the dataset comes from Troy Hunt, operator of the Have I Been Pwned service used to identify emails that appear in data breaches.
Hunt writes that a well-known tech company contacted him about Naz.API, a collection of one billion credentials. “Unlike similar lists that are merely collections of login names and passwords from previous data breaches, this dataset includes 25 million passwords that had never been leaked before,” he writes.
When we weren’t looking, @haveibeenpwned‘s Pwned Passwords rocketed past 7 *billion* requests in a month ð² pic.twitter.com/hVDxWp3oQG
– Troy Hunt (@troyhunt) January 16, 2024
Hunt found that Naz.API contained 319 files totaling 104GB and 70,840,771 unique email addresses. It impacted 427,308 individual HIBP subscribers, and 65.03% of the addresses are already in HIBP (based on a random sample set of 1,000).
The fact a third of the email addresses have never been seen in previous leaks is significant. In the forum post that included the database, the poster stated that it was created by extracting data from stealer logs. This form of malware attempts to steal data from infected machines, such as passwords, credit card details, crypto wallets, and more.
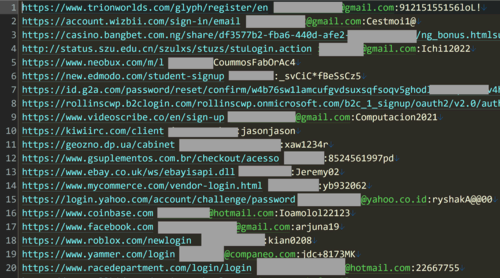
Hunt posted a screenshot of the dataset that showed some of the stolen data. The passwords appear in plaintext rather than being hashed and many are incredibly simple, commonly used strings. As we’ve seen so many times before and often warned against, there’s a huge number of people using the same password/email address combo across multiple services.
Hunt contacted some people on the list to confirm that their credentials are or were at one time accurate. He also confirmed that a selection of emails were associated with the named websites, which include Facebook, Roblox, Coinbase, Yammer, and Yahoo.
Not all of the data comes from stealer malware. A large percentage are the result of credential stuffing, which collates data from previous breaches. One of Hunt’s own passwords appeared in the data, though he hasn’t used it since pre-2011.
“Some of this data does not come from malware and has been around for a significant period of time,” he wrote. “My own email address, for example, accompanied a password not used for well over a decade and did not accompany a website indicating it was sourced from malware.”
To check whether your data appears in the Naz.API dataset or in any previous breach, visit Have I Been Pwned.