Facepalm: Punycode is an encoding technique designed to represent Unicode characters within the simpler ASCII character set. When used in conjunction with web addresses, Punycode characters provide cybercriminals with a powerful method to target new victims among unsuspecting internet users.
Punycode-enhanced techniques for spreading malware and cyber-attacks have been known since 2017 when a web developer created a proof-of-concept site that resembled apple.com. Punycodes remain highly effective today, especially when employed in a malicious advertising campaign that closely mimics legitimate websites.
According to Malwarebytes Labs, a recent campaign targeted the KeePass website using a malicious ad hosted on Google. Users were deceived with a fake web page impersonating the official site of the open-source password manager, KeePass. This campaign exploited a Punycode character to create a convincing imitation of the real webpage.
Malwarebytes analysts reported that the malicious ad was served in response to search queries for “keepass.” It was particularly deceptive because it displayed the official KeePass logo and URL, appearing before organic search results. This deceptive appearance made it nearly indistinguishable from the legitimate site. When users clicked on the ad, they were redirected to a seemingly secure (HTTPS) web page designed to mimic the official KeePass website.
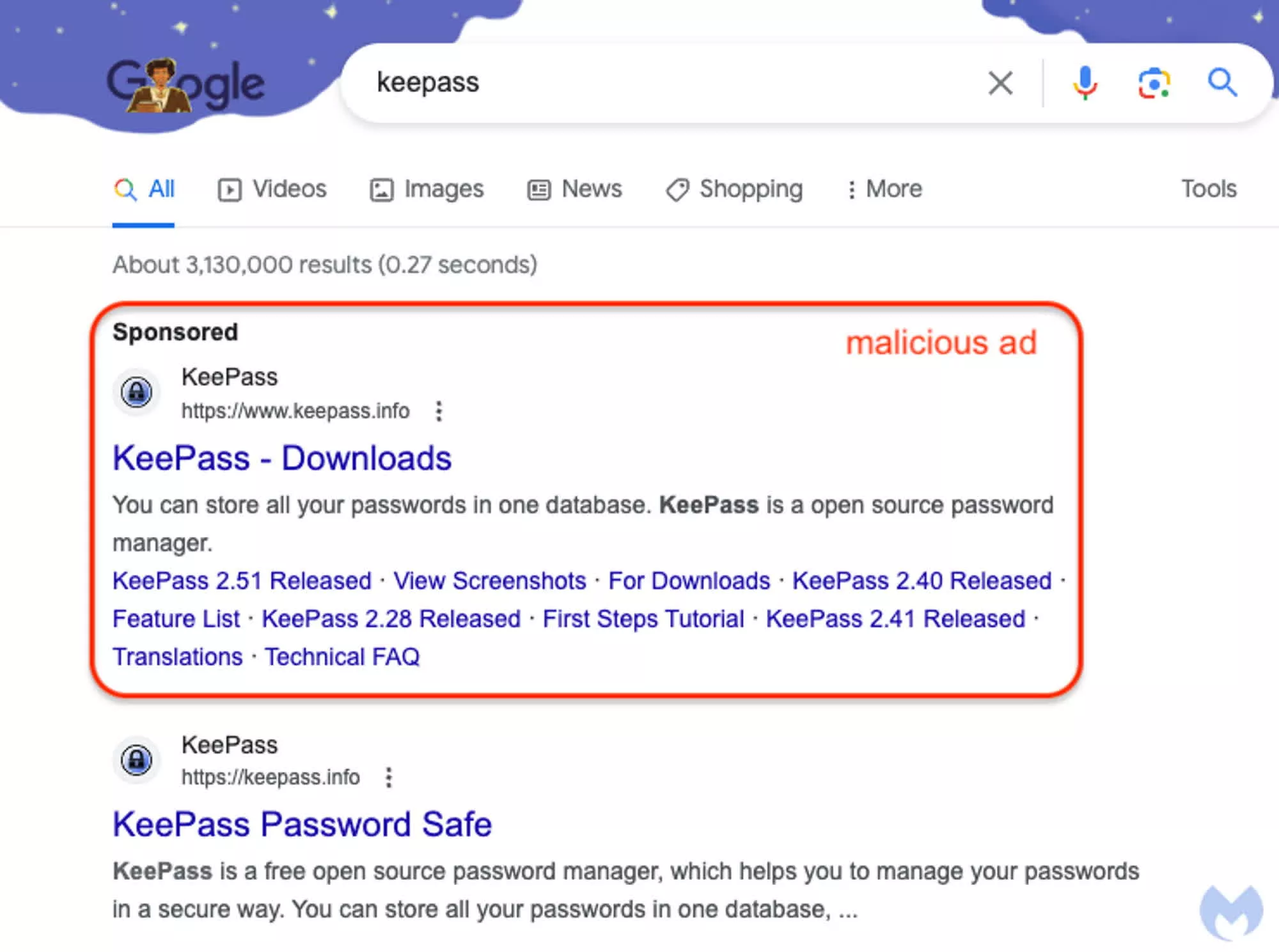
Malwarebytes discovered that the fake website was using Punycode to replace the initial “k” in the domain name. While Punycode is subtly employed, it effectively disguises the malicious nature of the real website, which is represented as “xn--eepass-vbb” dot info.
This fraudulent site offers a malicious .msix installer in place of the official KeePass download, which contains a PowerShell script associated with the FakeBat malware family. This script is intended to connect to a command and control server run by cybercriminals, enabling them to download a new malware payload onto the compromised system.
Threat actors have been using Punycode characters with internationalized domain names in phishing campaigns for years, as noted by Malwarebytes. The recent case involving KeePass demonstrates the ongoing effectiveness of this technique, particularly when combined with brand impersonation campaigns carried out through malicious ads hosted by Google. To mitigate the threat, users can manually enter the official URL in their browser or avoid clicking on “sponsored” messages displayed before genuine search engine results when seeking software downloads.

