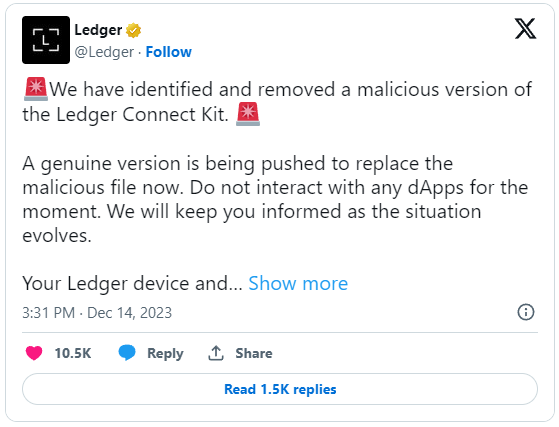
Ledger is warnings users not to use web3 dApps after a supply chain attack on the ‘Ledger dApp Connect Kit’ library was found pushing a JavaScript wallet drainer that stole $600,000 in crypto and NFTs.
Ledger is a hardware wallet that lets users buy, handle, and securely store their digital assets offline, supporting multiple cryptocurrencies, including Bitcoin and Ethereum.
The company offers a library called the “Ledger dApps Connect Kit” that allows web3 apps to connect to Ledger hardware wallets.
Today, Ledger warns users that its Ledger Connect Kit was compromised to include malicious code and that all users should avoid using dApps for now. This malicious code added to the library is a wallet drainer that automatically steals crypto and NFTs from wallets that connect to the app.
The malicious version of the library has been removed, and a new clean version of the kit, version 1.1.8, was uploaded on Ledger’s distribution channels at 2:35 pm CET. However, all potentially impacted projects must exchange their malicious version with a clean copy before they are safe to use again.
According to a notice on the impacted GitHub repository, the wallet drainer code affects versions 1.1.5 through 1.1.7 of the Connect Kit, injected into the package via a compromised NPM account.
Also, Ledger has advised users to ‘Clear Sign’ all transactions, following these instructions.
Users should avoid all interaction with any DApps until they have confirmed that those have moved to a safe version of the Connect Kit.
The company also warned of ongoing phishing attacks attempting to take advantage of the situation, advising users to remain vigilant for messages asking them to share their 24-word secret recovery phrase.
Ledger told Bleeping that its library was compromised after its NPMJS account was breached this morning during a phishing attack on a former employee.
“The attacker published a malicious version of the Ledger Connect Kit (affecting versions 1.1.5, 1.1.6, and 1.1.7).” Ledger told BleepingComputer.
“The malicious code used a rogue WalletConnect project to reroute funds to a hacker wallet.”
Ledger states that a fix was deployed 40 minutes after Ledger became aware of the breach and that the compromised library was only available for 5 hours.
Ledger has assured users that the core hardware (Ledger device) and the main software application (Ledger Live) used for managing cryptocurrency assets have not been compromised or directly affected by this supply chain attack.
The wallet drainer
Blockchain security firm SlowMist reports that the compromise started in Ledger Connect Kit 1.1.5 with the attacker leaving a message in the code, possibly as testing.
In versions 1.1.6 and 1.1.7 of the package, heavily obfuscated malicious JavaScript code was also implanted.
BleepingComputer analyzed the script to establish its functionality and found that it attempts to steal cryptocurrency and NFTs from Coinbase, Trust Wallet, and MetaMask.
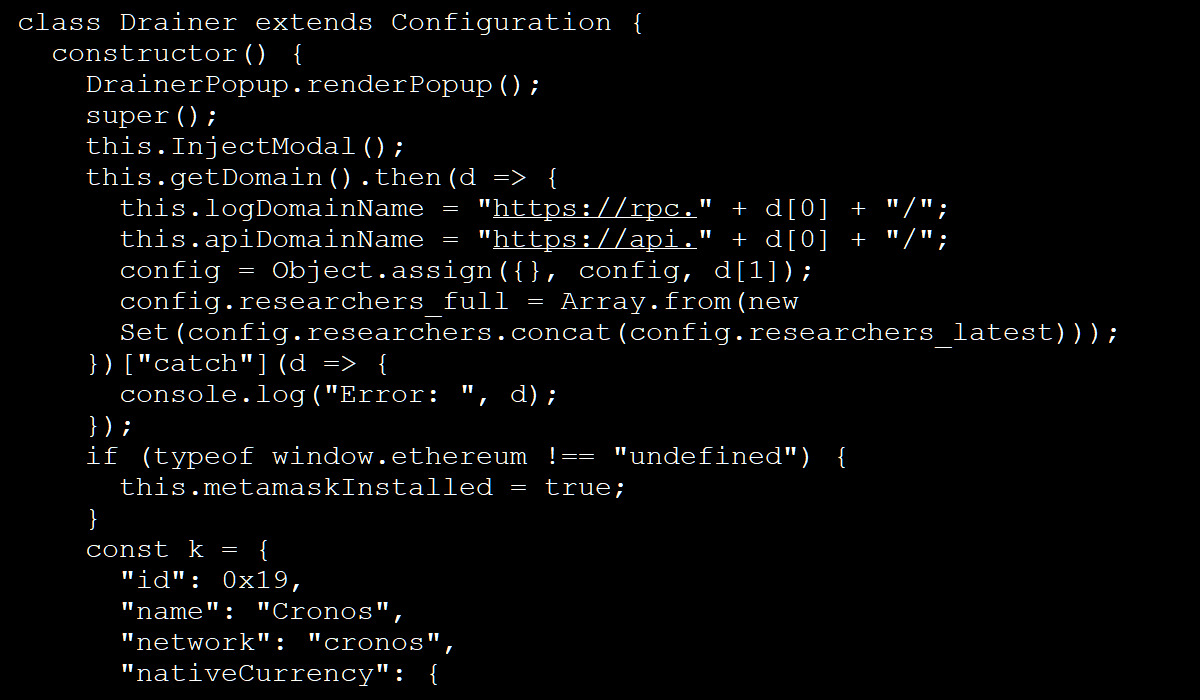
Source: BleepingComputer
At this time, the investigation into the incident is still ongoing, and the impact or actual losses of assets due to the deployment of the drainer have not been determined yet.
However, reports suggest that approximately $680,000 was stolen in the supply chain attack.
Ledger told BleepingComputer that they had reported the hacker’s wallet addresses and that Tether has frozen stolen USDT.
Ledger has promised to publish more details about the incident through a comprehensive report later today, but for now, they’re focusing on securing the library and investigating the breach.