Key Takeaways
- Look out for alarming subject lines that use words like “Urgent” or “Action Required.”
- Check the domain name for red flags, such as public domain email addresses or unusual top-level domains.
- Be wary of generic or overly personalized greetings, grammar and spelling mistakes, and requests for sensitive information.
Cybercriminals use phishing emails to steal from or hack you. They pretend to be a legitimate business or person, making you think you’re dealing with the real one. But if you look for these eight warning signs, you can avoid these emails.
1. Alarming Subject Line
Cybercriminals use social engineering, which is just targeted manipulation to convince a person (or organization) to reveal sensitive information. But in reality, you’re doing the opposite. A popular social engineering tactic is an alarming subject line.
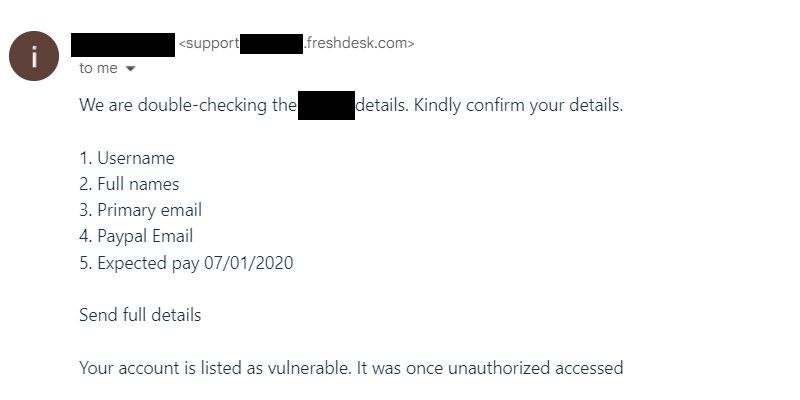
If the email’s subject line contains words like “Urgent,” “Time-Sensitive,” “Security Alert,” “Action Required,” or “Account at Risk,” you should be cautious. The would-be hackers hope you’ll go into panic mode you see those words. That way you react impulsively, and don’t think twice when they ask you to submit sensitive information, click a link, or download an attachment.
Keep in mind that legitimate businesses also use these subject lines to convey a real emergency to employees or customers. So you shouldn’t send that email to the trash bin just yet.
2. Suspicious Domain Name
The cybercriminals will also try to ensure the email looks legitimate. For example, they may use the name, logo, and email design of a reputable company. An example is the PayPal invoice scam.
But if you look closely at the domain of the email, you may find one of the following red flags:
- They’re using a public domain email address, such as company@gmail.com or company@yahoo.com.
- The domain name is a misspelling or variation (it can be very subtle) of one used by a genuine organization.
- The domain isn’t straightforward and contains some extra subdomains.
- The top-level domain is unusual, instead of the ones companies typically use (e.g., .com, .net, .org, or .co.uk).
If the domain looks suspicious, contact the company directly to find out. You can also visit the website and check the “About Us” page for the correct email address. Better yet, if you have previous correspondence with the business, check the legitmate domain against the one in the suspicious email.
3. Greeting is Generic or Too Personalized
Some phishing emails will start with a generic greeting. For instance, they may greet you with “Dear Customer,” “Dear [Service] User,” “To Whom It May Concern,” “Dear [username on email address],” or simply “Greetings.” Many companies will use your first name since they probably know it through their KYC initiatives.
If the hackers know your name, they may over-personalize the greeting to establish trust. They might include information that is too personal or specific, such as your full name, phone number, and address. Legitimate businesses will create a balanced greeting that doesn’t include information you already know about yourself.
4. Grammar and Spelling Mistakes
When a legitimate company sends an email, it will ensure it has correct grammar and spelling. A phishing email, on the other hand, may have obvious errors. That’s because some of these phishing emails are written rather quickly and by non-native speakers.
5. Contains Suspicious Links and Attachments
Phishing emails may contain links that direct you to malicious websites. Those sites may contain a form asking for your sensitive information. The form might even look like one found on a genuine website.
For example, it may look like the Google or Facebook sign-in page. But the moment you enter your username and password, the cybercriminal will be able to see what you’re typing on their end. Then, they will use that information to hack into your account.
If it’s not a link, the email might include an attachment. That attachment is usually an executable file (EXE) or compressed archive (ZIP, RAR, or TAR.GZ) file. The aim is to infect your device with malware or ransomware once you download and open it.
6. Requests Sensitive Information
No legitimate organization would ask for your sensitive information over an email. You shouldn’t respond to an email if it asks you for your password, credit card information, account balance, address, phone number, or similar details.
Also, you shouldn’t reply if the email asks for general information about yourself, such as your mother’s maiden name, favorite color, or pet’s name. Hackers can use this information to bypass the security questions on your online accounts.
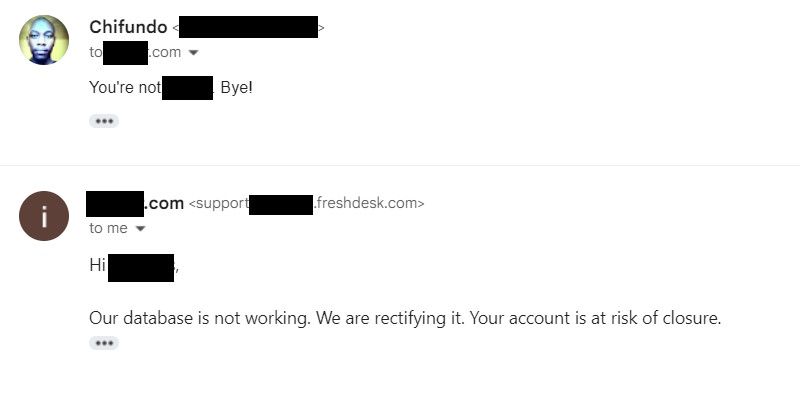
7. Communicates a False Sense of Urgency
To get you to do what they want, the cybercriminals might tell you to take immediate action to avoid some negative outcome. That way, you don’t have the time to verify anything they’re saying if you’re in panic mode. For instance, they might say that if you don’t click on the link or if you don’t provide the information they’ve requested, your account may be closed or charged.
Contains an Unrealistic Offer
If you’ve suddenly won some sweepstakes you never entered, or a relative you’ve never heard of has died and left you a hefty inheritance, it could be a phishing email. These cybercriminals will try to convince you to provide them with certain information to access the money or claim a prize. In some scenarios, they might request a processing fee for you to get the money you’ve won or inherited.
What to Do When You Get a Phishing Email
Learning what to do when you receive a phishing email can help you avoid being scammed. The most important rule to remember is that you should not click on anything or provide any information.
Also, email phishing is just one type of phishing. So stay educated and learn how to avoid those other scams as well.
Don’t be paranoid with every email you receive asking you for something. While phishing emails are designed to confuse you, if you know what they look like, they aren’t hard to spot. A majority of the time you’ll be able to quickly tell when an email is legit or a scam.