
The Pwn2Own Toronto 2023 hacking competition has ended with security researchers earning $1,038,500 for 58 zero-day exploits (and multiple bug collisions) targeting consumer products between October 24 and October 27.
During the Pwn2Own Toronto 2023 hacking event organized by Trend Micro’s Zero Day Initiative (ZDI), security researchers targeted mobile and IoT devices.
The complete list includes mobile phones (i.e., the Apple iPhone 14, Google Pixel 7, Samsung Galaxy S23, and Xiaomi 13 Pro), printers, wireless routers, network-attached storage (NAS) devices, home automation hubs, surveillance systems, smart speakers, and Google’s Pixel Watch and Chromecast devices, all in their default configuration and running the latest security updates.
While no team signed up to hack the Apple iPhone 14 and Google Pixel 7 smartphones, the contestants hacked a fully patched Samsung Galaxy S23 four times.
The Pentest Limited team was the first to demo a zero-day in Samsung Galaxy S23, exploiting improper input validation weakness to gain code execution, earning $50,000 and 5 Master of Pwn points.
The STAR Labs SG team also exploited a permissive list of allowed inputs to hack Samsung’s flagship on the first day, earning $25,000 (half prize for the second round of targeting the same device) and 5 Master of Pwn points.
Security researchers with Interrupt Labs and the ToChim team also hacked the Galaxy S22 on the second day of the competition by exploiting a permissive list of allowed inputs and another improper input validation weakness.
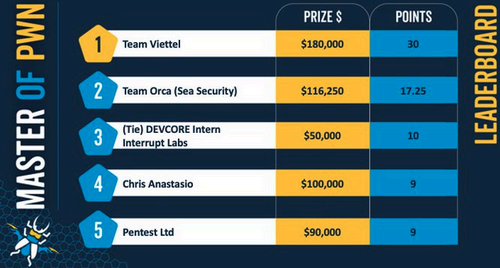
Team Viettel won the competition, earning $180,000 and 30 Master of Pwn points. They are followed on the leaderboard by Team Orca of Sea Security with $116,250 (17.25 points) and DEVCORE Intern and Interrupt Labs (each with $50,000 and 10 points).
The security researchers have successfully demoed exploits targeting 58 zero-days in devices from multiple vendors, including Xiaomi, Western Digital, Synology, Canon, Lexmark, Sonos, TP-Link, QNAP, Wyze, Lexmark, and HP.
You can find the complete schedule of the competition contest here. The full schedule for Pwn2Own Toronto 2023’s first day and the results for each challenge are listed here.
Once zero-day vulnerabilities exploited during the Pwn2Own event are reported, vendors have 120 days to release patches before ZDI publicly discloses them.
In March, during the Pwn2Own Vancouver 2023 competition, competitors won $1,035,000 and a Tesla Model 3 car for 27 zero-day (and several bug collisions).

