In a world where software is produced, distributed, and re-distributed, how do you ensure the software you consume is authentic and safe for your environment? How do you know the software you deployed yesterday is safe today? Most software exploits are discovered after the software has been deployed, which raises the question:
“How do software vendors produce incremental information, and how do consumers get updated information from trusted sources?”
It’s not just about getting software updates, as the majority of exploits are distributed as updates. Staying updated isn’t the most secure. Staying informed, to guide the decisions in your organization is.
Making Informed Decisions, From Trusted Sources
How do you stay informed about your favorite personal topic? Do you listen to one friend or colleague? Or do you aggregate information from multiple sources, each with its own context and scope of trust? Your friend Jay may provide great information about construction projects, and your other friend Chris may have great stock tips. They may both be sources you trust, but Chris may not be the best person to trust for your new kitchen rebuild.
Staying informed about your software means consuming information from various sources and knowing when and where to apply that information.
To illustrate the scenario, consider these three fictitious companies:
- Synsation Corp produces and maintains multiple versions of their net-monitor and net-aggregator software products
- Cosmic Security is an independent security company that monitors for vulnerabilities and potential environmental configuration issues
- ACME Rockets consumes some of Synsation Corp’s software and subscribes to Cosmic Security for monitoring their various environments and network security
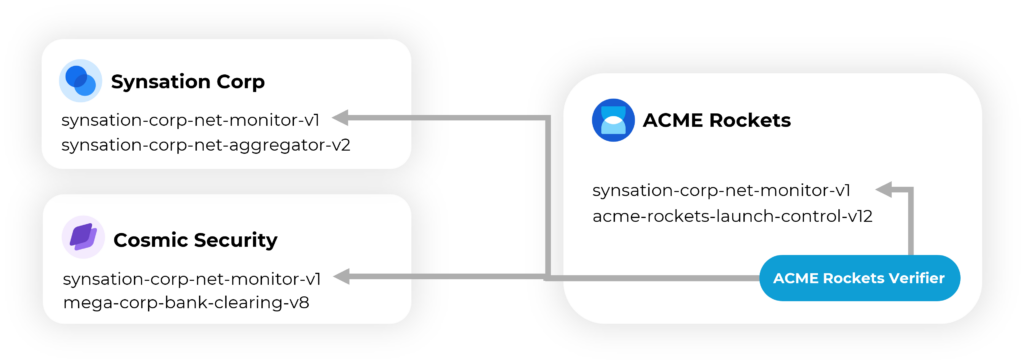
The multiple sources (Synsation Corp and Cosmic Security) inform ACME Rockets on how to proceed. ACME Rockets IT and Security teams can tune their environment for which feeds of information they choose to trust. They chose to trust security insights from Cosmic Security. ACME Rockets can add information for how and when the software can be distributed in their environment or make different decisions for different environments. They may have different rules for their development and production environments. ACME Rockets may have critical launch control systems they need to be more concerned about the stability of the environment, compared to other environments.
Businesses must make informed decisions, from trusted sources.
If a new vulnerability is discovered in currently deployed software, should ACME Rockets immediately disable that software? Is disabling that component more impactful to the business than the potential risk of the vulnerability? Could the “update” cause more damage than the potential risk? How would they verify the identity of the source of information that’s saying the software is vulnerable? These are just a few examples of questions businesses face daily.
Consuming Information Updates
Software vendors have created automated update mechanisms, but how do companies consume automated information updates? Is monitoring email or trolling various websites and social media effective in automating the core of your business? And, how do you know you can trust the information?
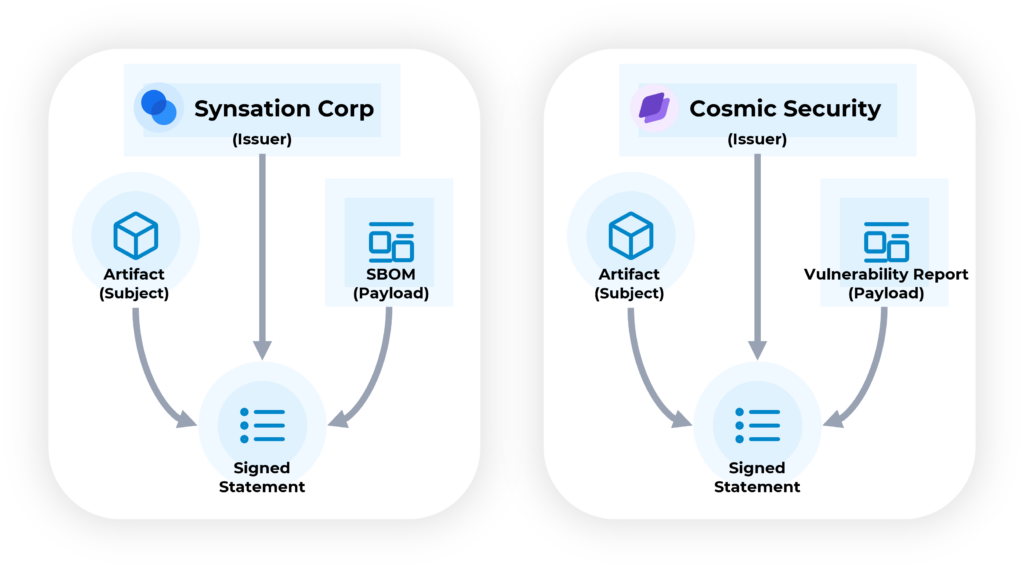
DataTrails implements evolving IETF Supply Chain, Integrity, Transparency & Trust (SCITT) standards, providing vendor interoperability. Referencing the SCITT Architecture, each software package, product, or service is known as an artifact by which information is published. The originating vendor (known as an Issuer) creates an identifier (subject) by which various issuers can publish information (the payload of a signed statement) about the same versioned artifact. The issuers of information sign the payload, providing a verifiable identity for the source of information. Each vendor can produce a separate feed of signed statements (filtered by the subject), enabling vendors to create multiple statements about the same artifact. Multiple issuers (Synsation Corp, Cosmic Security) can provide signed statements about the same artifact using the subject, and hosting their own SCITT Transparency Service. Consumers of the feeds, such as ACME Rockets, can evaluate the information, signed by issuers they trust.
Consuming information is similar to asking friends, colleagues, or “the internet” about a particular product, movie, or restaurant. You choose which sources (SCITT Transparency Services) you seek for information. Each references the same product, movie, or restaurant, and you weigh their opinion based on how much you trust the source, and if the context matches yours. As humans, we associate an identity with the information and the context for how to apply that information. We make judgments about who we trust for particular contexts. The SCITT specifications model that same concept.
Granularity of Information and Evaluating Risk
Synsation Corp may publish information stating version 1 of their net-monitor software is no longer supported, identifying a newer version. Or they may publish a newly discovered network egress vulnerability. Historically, Synsation Corp might revoke the signing key for that software, but that’s a big binary switch, creating a larger blast radius. When a key is revoked, consumers don’t know if the identity was stolen, or the vendor is acknowledging a specific issue with a specific released product. There’s no granularity, enabling consumers to make educated decisions.
Using DataTrails and SCITT, Synsation Corp can publish a signed statement, saying the particular versioned product is going out of support on a particular date, and there’s a specific vulnerability in that version of their product. The identity isn’t stolen, enabling ACME Rockets to continue trusting software from Synsation. ACME Rockets simply needs to evaluate the specific issue, for their context.
As a consumer of the net-monitor software, ACME Rockets deploys their software within isolated network boundaries, with no egress capabilities, These security measures minimize the potential impact, giving ACME Rockets some choices. Without verifying the new version will function as expected, they have can evaluate the payload of the signed statements and make informed decisions to manage their risk. They can create new signed statements on their instance of DataTrails stating version 1 of the net-monitor (identified by the same subject) is still approved for existing environments. This enables nodes to scale and re-initialize as ACME Rockets can safely verify the signed statements for their context. They can also block new deployments from consuming the concerning version 1 of net-monitor.
ACME Rockets can register additional signed statement stating the specific versioned software must be updated within 30 days (identifying the specific date). This gives the ACME Rockets operational teams time to remediate the known issue, without assuming the risk of blindly updating to a new version which might pose more risk. Remember, most vulnerabilities were deployed as updates.
Creating Data Trails
Industry leaders, like DataTrails, are contributing to and adopting these new standards addressing the challenges of Integrity, Transparency, and Trusted updates. Using the IETF SCITT standards with DataTrails, your company can consume, create, and maintain trusted, immutable information to secure your supply chain with the granularity required to manage your environments.
Being able to distribute, consume, and tailor information to your environment matches the way humans interact and share information. We can choose to listen to or ignore information we get from trusted and untrusted sources, and tailor that information to the context in question. Having a standard way to communicate information enables your company to scale while focusing on the core aspects of your business.
Try DataTrails and SCITT today: Getting Started with SCITT

