The Cisco Talos Year in Review report released Tuesday highlights new trends in the cybersecurity threat landscape. We’ll focus on three topics covered: the ransomware cybercriminal ecosystem, network infrastructure attacks and commodity loader malware.
More ransomware actors switched to extortion rather than encryption, while commodity loaders evolved to be stealthier and highly effective, although new major security improvements have seen the day in 2023, such as Microsoft Office disabling macros by default. Network devices are increasingly impacted by cybercriminals and state-sponsored threat actors.
Jump to:
The ransomware cybercriminal ecosystem changed
Most targeted vertical
In terms of ransomware, the most targeted vertical, as observed by Cisco Talos in 2023, was the healthcare and public health sector, which is not surprising since the organizations in that sector often suffer from underfunded budgets for cybersecurity and low downtime tolerance (Figure A). In addition, those organizations are interesting targets because they possess protected health information.
Figure A
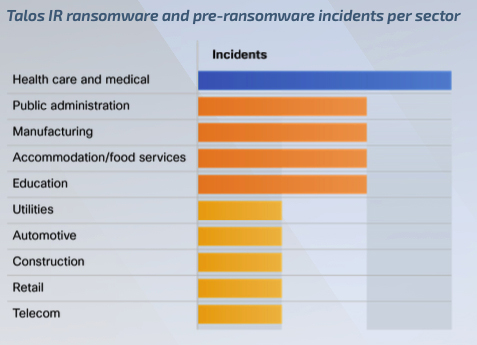
Some ransomware groups have been changing
The most active ransomware group for the second year in a row was LockBit (25.3% of the total number of posts made to data leak sites), followed by ALPHV (10.7%) and Clop (8.2%).
Yet some ransomware groups kept changing in 2023; those structures often merged or rebranded in an attempt to confuse law enforcement and researchers tracking them. The cybercriminals active in the field often work for several ransomware-as-a-service services at the same time.
Multiple leaks of ransomware source code and builders also affected the ransomware threat landscape because these allowed more people (even those with little technical knowledge) to start their own operations.
Zero-days exploited at an unprecedented pace
Highly technical actors have been exploiting zero-day vulnerabilities at an unprecedented pace. The Clop ransomware group in particular has been able to exploit multiple zero-day vulnerabilities, including vulnerabilities in the GoAnywhere MFT platform, MOVEit and PaperCut.
Cisco Talos states that “Clop’s repeated efforts to exploit zero-day vulnerabilities is highly unusual for a ransomware group given the resources required to evolve such capabilities,” yet it is still unsure that they do evolve exploits on their own. When questioned about it in an email interview, a Cisco spokesperson told TechRepublic, “Because of the murkiness in the relationships that constitute the ransomware ecosystem, it can be difficult to accurately parse out which personnel/organizations are responsible for which actions. Because of this, we do not have direct insight into how Cl0p obtained the 0days and have not observed any indications that they purchased them. Regardless of whether they developed them themselves or purchased them, the usage suggests Cl0p is well-resourced, either in engineering talent or in finances and connections that would allow them to acquire from a third party.”
More affiliates are using a data theft extortion model
Another remarkable shift in the ransomware threat landscape is that more affiliates are now switching to a data theft extortion model rather than the usual encryption model. In these attacks, cybercriminals do not deploy ransomware; instead, they steal organizations’ sensitive information before asking for a ransom.
The improvements in ransomware detection capabilities from Endpoint Detection and Response and Extended Detection and Response software might be one reason for switching tactics and stopping deploying ransomware on the targeted systems. Cisco Talos also suspects the aggressive pursuits from U.S. and international law enforcement against ransomware actors might be another reason for that change.
Network infrastructure attacks increased
Cisco Talos observed an boost in attacks on networking devices in 2023, particularly attacks operated by China- and Russia-based groups looking to advance espionage objectives and ease stealthy operations against secondary targets. The researchers observed such activity from other cybercriminals, including initial access brokers and ransomware threat actors.
Weak security on network devices
Networking devices, although being key components to any organization’s IT infrastructure, are not often examined from a security point of view and are often poorly patched, making them an interesting target for cybercriminals. Yet those devices often run on non-standard operating systems, rendering their exploitation harder by cybercriminals but also unmonitored by standard security solutions.
The typical compromise of those devices starts with threat actors exploiting unpatched vulnerabilities, weak or default credentials, or insecure device configuration.
A Cisco spokesman told TechRepublic that “the continued prevalence of default credentials may be partly explained by the sheer number of vendors and products combined with the lack of uniform standards/best practices. The proceed away from default credentials should certainly help better the situation. It is important to note that weak credentials can also be exploited if the actor is able to brute-force or password-spray, and that access brokers still reach success in obtaining credentials and selling them on the dark web. This means that even if organizations are not using default credentials, it’s essential they create unique and complex passwords, use MFA where possible, and emphasize additional security measures such as segmentation and IR planning as well.”
Targeted devices had a high severity score
Vulnerabilities affecting network devices in 2023 all had a high severity score, meaning those devices were easily exploitable and had the potential to provoke significant operational impact, according to Cisco Talos.
Once compromised, those devices allow attackers to capture sensitive network information, facilitating encourage access to the target’s networks. Attackers also might plant malware on the devices to establish an initial foothold in the target’s infrastructure without the need for any authentication, or to redirect network traffic to actor-controlled servers. Finally, the devices are also often used by attackers as anonymization proxies for conducting attacks on other targets.
Commodity loader malware evolved
Commodity loader malware such as Qakbot, Ursnif, Emotet, Trickbot and IcedID have been around for years. They were initially banking trojans, looking for credit card information theft on infected computers.
In late 2023, new variants of IcedID and Ursnif appeared with a striking difference as compared to their older versions: Their banking trojan capabilities had been removed, and their dropper functionalities had been improved. The IcedID new samples have been used by initial access brokers known for commonly selling network accesses to ransomware groups. The latest Ursnif variants were used by the Royal ransomware group.
Qakbot also evolved, deploying new features ideally suited to help ransomware groups.
This evolution from banking trojan to loader is attractive for cybercriminals who want to be stealthier; the banking trojan function removal renders those malware less detectable.
The infecting vector for Qakbot, IcedID and Ursnif evolved, as Microsoft’s new security measures on Office products affected the malware threat landscape, forcing cybercriminals to find new ways to use macros undetected or avoid using them completely (Figure B).
Figure B
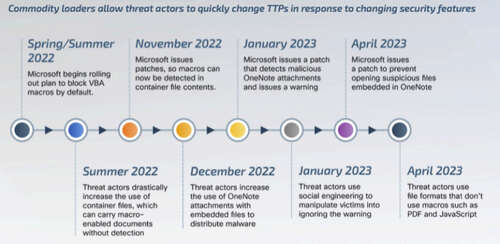
Threat actors used different methods compared to previous years for spreading their malware and infecting devices, such as using JavaScript, PowerShell, OneNote documents, or HTA files, to name a few. They also used the Google Ads platform to deploy malware such as Ursnif, IcedID or Trickbot, fully avoiding macros.
Some other threat actors deploying Emotet, IcedID and Ursnif have been observed using older methods with macros, probably because the success rate on unpatched enterprise legacy systems is still high.
How to protect your business from these cybersecurity threats
The threat landscape evolves to suit cybercriminals’ needs, and your security team needs to ensure its mitigation strategies are keeping up with the trends. Here are some tips for securing your business from these cyberthreats. In addition, all operating systems and software must be up to date and patched to avoid being compromised by common vulnerabilities.
Ransomware
Access control mechanisms should be carefully reviewed in all corporate environments, and data segmentation should be applied for storing sensitive data because ransomware threat actors are increasingly trying to steal sensitive data rather than encrypt it.
Network devices
Network devices must be up to date and patched. Default passwords, if any, must be changed to strong passwords. All of the devices’ configuration files should be carefully analyzed and tuned to avoid any malicious exploitation. When possible, multifactor authentication must be deployed on those devices. Also, inbound and outbound communications from the devices should be monitored to detect malicious communication.
Commodity loaders
The main families of commodity loaders have dropped their banking trojan capabilities to be lighter and stealthier, even without using macros — often to ease ransomware operations. Organizations should educate their employees to handle more file types with caution, such as PDF files or ZIP archives that might contain malicious files.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

