Join us in returning to NYC on June 5th to collaborate with executive leaders in exploring comprehensive methods for auditing AI models regarding bias, performance, and ethical compliance across diverse organizations. Find out how you can attend here.
With attackers setting speed records for breakouts and tool download times, every security operations center (SOC) team needs to consider how AI can help bend time in their favor.
It takes just two minutes and seven seconds to move laterally within a system after gaining access, and just 31 seconds for an attacker to download a toolkit and start reconnaissance operations on a compromised system. These figures are from George Kurtz, president, CEO, and co-founder of CrowdStrike. He provided the statistics during his RSAC 2024 keynote Next-Gen SIEM: Converging Data, Security, IT, Workflow Automation & AI.
“The speed of today’s cyberattacks requires security teams to rapidly analyze massive amounts of data to detect, investigate and respond to threats faster. This is the failed promise of SIEM [security information and event management]. Customers are hungry for better technology that delivers instant time-to-value and increased functionality at a lower total cost of ownership,” said Kurtz in his keynote. “The vast majority of the critical security data is already resident in the Falcon platform, saving the time and cost of data transfer to a legacy SIEM. Our single-agent, single-platform architecture unifies native and third-party data with AI and workflow automation to deliver on the promise of the AI-native SOC,” he said.
Legacy SIEMS make data challenges worse
Attackers are becoming more adept with their tradecraft in finding gaps between endpoint and identity security. Endpoint data often holds invaluable insights that, aggregated over time, can predict intrusion and breach attempts.
“One of the main problems in security is a data problem, and it’s one of the reasons why I started CrowdStrike. It’s why I created the architecture that we have, and it’s incredibly difficult for SOC teams to be able to sort through this massive amount of data and volumes to find threats,” Kurtz told the audience.
Legacy SIEMs are quickly becoming more of a liability than an asset to SOC teams relying on them. SOC Analysts have long called the need to use multiple, conflicting systems “swivel chair integration.” Having to turn from one screen to the next and compare incident data burns valuable time, while the systems often produce conflicting data. SOC Analysts then have to run each data source through tools to see if the risk scores match. Legacy SIEMs are also known for having slower search speeds and limited visualization options.
“It can take days to ingest data can take days to actually get through queries. So if you want to find and investigate an alert, you can’t be waiting days, particularly when you’re trying to triage an incident and it all goes back to that concept of how do you bend time and how do you actually move faster than the adversary,” said Kurtz during his keynote.
Kurtz used the allegory of how quickly cell phone plans progressed from limited minutes to unlimited caps on use to explain how next-generation SIEMs can be cost-effective. Kurtz believes next-gen SIEMs should allow for scalable data ingestion without exponential cost increases, driving better security decisions free of financial constraints. Kurtz says next-gen SIEM needs to break the cost productivity curve so customers can scale and ingest every source of available data they have.
The goal: Bend time in favor of defenders
In launching a series of CrowdStrike Falcon Next-Gen SIEM innovations last week at RSAC 2024, Kurtz went all in on why it’s so important that defenders have the apps, tools and platform they need to bend time in their favor. A core message of his keynote is that it’s time to remove the roadblocks of legacy SIEM and strengthen Security Operations Centers (SOCs) with AI-driven expertise. CrowdStrike is offering all Falcon Insight customers 10 gigabytes of third-party data ingest per day at no additional cost so they can first experience the speed and performance of Falcon Next-Gen SIEM.
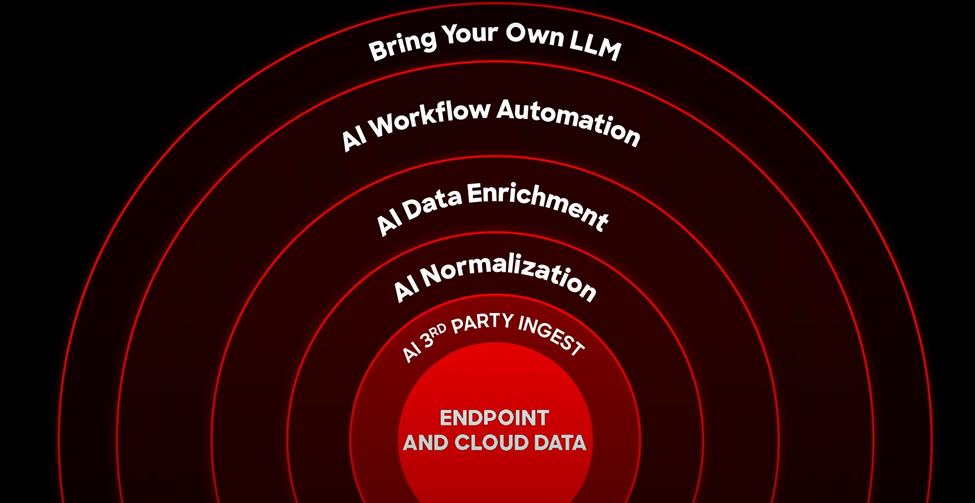
AI is a core part of Falcon Next-Gen SIEM architecture. Kurtz explained that their approach to AI as part of next-gen SIEM is to automate data parsing and normalization, enrich data to better identify and prioritize threats, and support advanced threat detection and automated response mechanisms.
Kurtz says that, by definition, an AI-native SOC is self-learning. He says every company has many learnings about their employees, threats and environment. He cautioned that companies shouldn’t just rely on vendors to provide that data and insights. “The system should actually learn about what a malicious insider looks like in your organization. It should learn about the threats you deal with and how they’re exploited. And it’s part of the adaptive retraining of the system as time goes on,” Kurtz explained.
Source: George Kurtz’s RSAC 2024 keynote Next-Gen SIEM: Converging Data, Security, IT, Workflow Automation & AI.
CrowdStrikes’ SIEM aims to accelerate SOC performance
Proving faster search performance and lowering the total cost of ownership is how CrowdStrike is positioning its Falcon Next-Gen SIEM versus the many legacy SIEMs in use today.
Claiming up to 150x faster search performance and an 80% lower total cost of ownership than legacy SIEMs and solutions positioned as SIEM alternatives, CrowdStrike is going to the heart of what most SOCs disklike most about legacy SIEM systems: slow performance and response times.
Key areas of innovation include generative AI, workflow integration, rapid data ingestion, and improved incident workbench solutions to further support SOC analyst productivity. Each area is summarized below:
Generative AI and Workflow Automation:
- Charlotte AI for all Falcon Data: Charlotte AI, CrowdStrike’s Generative AI security analyst, is now available for Falcon data in Next Gen SIEM. SOC analysts can ask for Falcon data in the Falcon platform, product documentation, or Knowledge Bases in plain language for a solution in seconds.
- Investigate with Charlotte AI: Automatically correlates all related context into a single incident and generates an LLM-powered incident summary for security analysts of all skill levels, speeding up investigations.
- New gen AI Promptbooks: New out-of-the-box promptbooks accelerate detection, investigation, hunting and response for most analyst workflows. Teams can define custom prompts to standardize and reuse detection and response workflows to move from incident to action faster.
- Native SIEM and SOAR Integration: The new Falcon Fusion SOAR UI gives SOC analysts the ability to drag and drop playbooks and workflows to speed up detection, investigation, and response. A growing library of integrations and actions automates critical security and IT use cases across teams and tools in Falcon Next-Gen SIEM.
- Automated Investigations and Threat Hunting: Falcon Fusion SOAR automates threat-hunting workflow. Falcon Next-Gen SIEM analysts can automatically query all data and visualize or orchestrate Falcon and third-party tool action to close the loop.
Rapid Data Ingestion for Enhanced Detection and Response:
- Expanded Data Ecosystem: New connectors in Falcon Next-Gen SIEM integrate third-party IT and security data into the Falcon platform.
- New Cloud Connectors: Includes complete AWS, Azure, and GCP connectors. AWS covers all key cloud services like GuardDuty, Security Hub and S3 Access Logs. Microsoft Defender for Cloud and Exchange Online are Azure connectors.
- Automated Data Normalization: New parsers simplify data onboarding. Automated third-party data normalization on the new CrowdStrike Parsing Standard enables rapid, accurate detection and response across all data sources.
- Automated SIEM Data Onboarding: New data management capabilities make it easy to understand the health, volume and status of data ingestion, as well as manage and edit custom parsers to easily bring in new data sources, including on-premises log collectors.
A Modern Analyst Experience with Incident Workbench Innovations:
- Automated Incident Enrichment: New automated enrichment capabilities add context to indicators SOC analysts add to an incident for complete Falcon platform context, including adversary TTPs, host and user data and vulnerabilities, reducing investigation time.
- Case Management and Incident Collaboration: Customized views, direct access to Advanced Event Search from the Incident Workbench, severity, and naming modification and automated change notifications when another analyst adds a note boost SOC analyst collaboration and ease of use.
- Add Threat Intelligence with Custom Lookup Files: Add threat intelligence or custom content to Falcon Next-gen SIEM to drive searches without manual processes.

