Sanctioned banks in Russia are getting around Apple’s App Store Review process to stay in the App Store. Here’s how they’re doing it.
Apple does what it can to stay within the laws of the countries it operates in, and that includes cultivating its regional App Stores to keep out apps affected by sanctions. That doesn’t stop companies who are effectively banned from the App Store from trying to stay in it.
Sanctions against Russian banks over the country’s military activity in Ukraine from February 25 forced Apple into removing a number of apps from the App Store, and cutting access to Apple Pay. The sanctions, from the EU and United States, effectively prohibited access to accounts from major Russian banks.
While Russian banking apps are banned from the App Store due to the sanctions as Apple is an American entity, bank customers in the country cannot access their accounts from their devices. To try and get around this, banks are using trojan horse apps to gain access to the App Store.
In a tweet thread on X, developer “Wukko” reveals a recent example of the Russian bank Sber thwarting the App Store Review process by hiding its banking app within another.
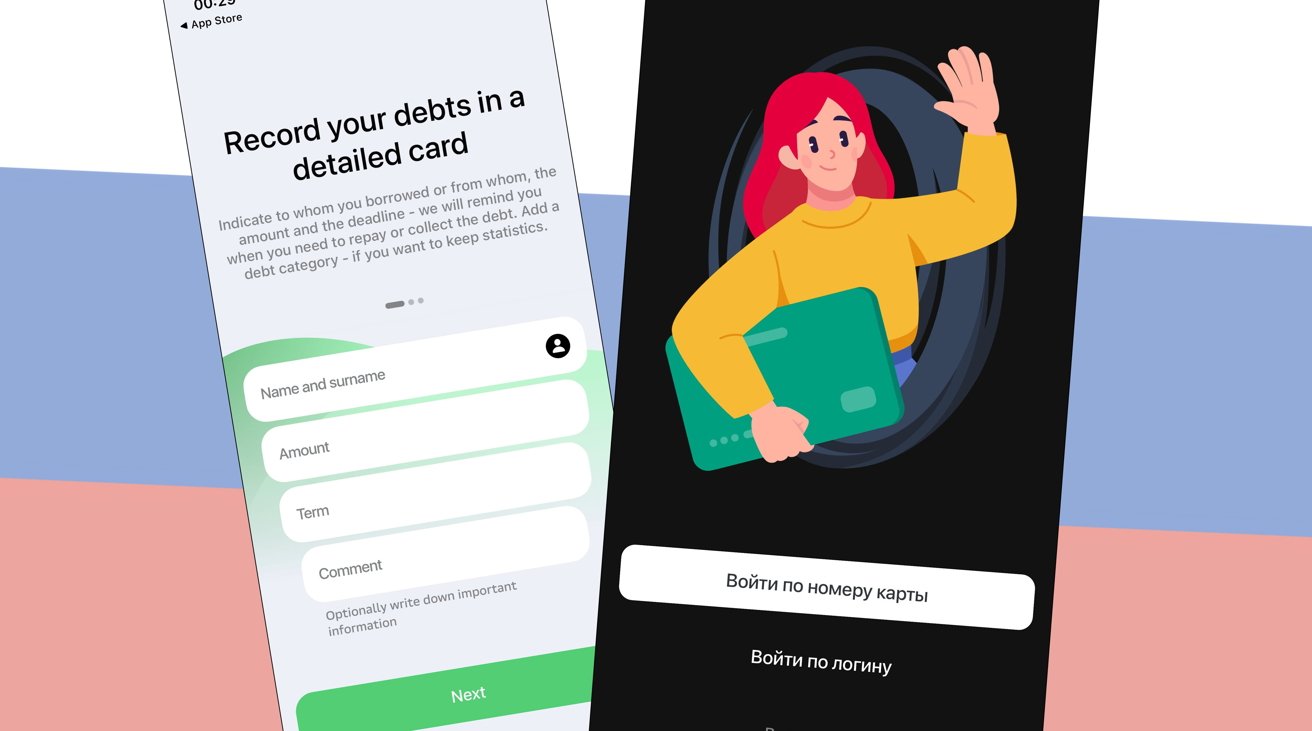
The app, released by a developer identified as “Prabhleen Hora” was presented as a fake lending tracking app. Crucially for the ruse, the lending app appearance was only shown in Western countries, but Russian users instead saw the banking app.
recently sber released yet another mock app that pretended to be a lending tracking app, which shortly got taken down
it pretends to be a lending app only in western countries (left), but if your ip is detected as russian, it lets you into the real part of the app (right) pic.twitter.com/EBexD6hGxa
— wukko (@uwukko) February 12, 2024
The app functioned by detecting the user’s IP, then showing the version of the app for that intended audience. A configuration file is requested from a third-party server as the app starts up, with the file changing depending on the user’s IP address.
The domain “trbcdn.net” that the file is hosted on is owned by CDN Video, which in turn is owned by Cloud.ru, and was previously Sbercloud.com
While it is plausible the App Store Review process was tripped up by the changing config file check,Wukko offers that Apple could’ve smelled something fishy about the app from its version history. The first iteration of the app in the App Store was “just libraries” at about 37MB, rising to 57.8MB for the second version, consisting of a mock accounting app.
The third iteration, which includes the proper banking app itself, shoots up to 232.8MB, a 175MB increase over the previous version.
Wukko adds that, if you drop the file path for the config file link, the address takes you to the APK page for Sber’s Android version.
Multiple trojan banks
Sber is not the only bank doing this, according to the tweeter. Tinkoff, another sanctioned bank, also released its own trojan horse app, using a vaguely similar trick.
The app, InvestCalendar, requested a config file from Firebase. However, Firebase blocks all requests from outside Russia, meaning the config file to switch the trojan over is only received by users in Russia.
That app also saw bumps in file size, starting from just 5.2MB and rising to 159.6MB.
“The point of this thread is to show that apple doesn’t really check apps on app store, and is picky only when it benefits them, not their users,” Wukko writes, before offering “insane respect” to the banks for still providing apps to customers in the “current political climate.”
While expressing that the “amount of effort [the banks] put into these undercover apps is crazy,” Wukko does offer a more sobering warning about the technique. “This can easily be abused to spread malware instead of innocent banking apps.”
Apple has since taken action against the apps to remove them from the App Store.
The App Store Review guidelines includes elements prohibiting apps with fake features from being submitted, as well as a rule that apps for financial trading, investing, and money management must be submitted by the financial institution itself. Apps are also forbidden from “arbitrarily restricting who may use the app, such as by location or carrier.”